Firewalld is a dynamic firewall management tool for Linux systems that simplifies network traffic control using zones, which define the trust level of network interfaces. It allows real-time configuration changes without needing to restart the service. It also supports a rich set of rules based on protocols, ports, services, and IP addresses, and offers predefined service definitions for ease of use. The tool can be managed through command-line tools (firewall-cmd) or graphical interfaces (firewall-config) This makes it a versatile and user-friendly solution for maintaining network security.

What is a Dynamic Firewall Manager?
A “dynamic firewall manager” is a system that allows for automated and real-time adjustments to firewall rules based on changing network conditions, threat intelligence, or other factors, essentially creating a “dynamic firewall” that can adapt to evolving security needs without manual intervention, unlike a traditional static firewall with fixed rules. It typically utilizes data analysis and automation to proactively detect and respond to potential threats.
What is the Architecture of FirewallD?
The core layer and the D-Bus layer on top make up the two layers of a firewall. Configuration and back ends such as iptables, ip6tables, ebtables, ipset, and the module loader are handled by the core layer.
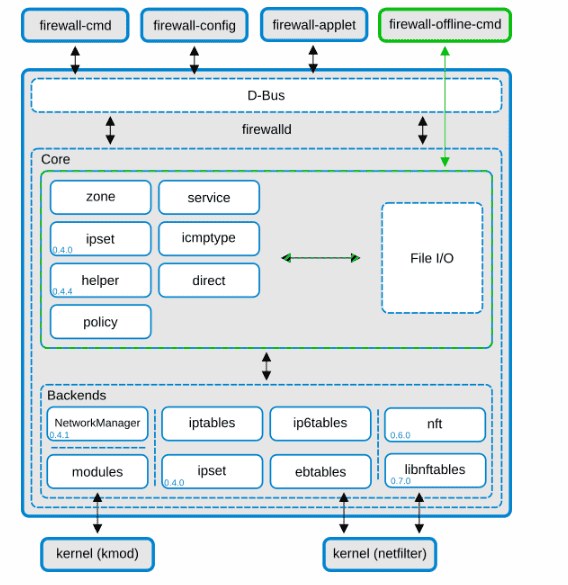
The main method for creating and modifying the firewall configuration is through the firewalld D-Bus interface. All the firewalld online tools, such as firewall-cmd, firewall-config, and firewall-applet, use the D-Bus interface. Instead of communicating with firewalld, firewall-offline-cmd uses the firewalld core and IO handlers to create and modify firewalld configuration files. Although it is possible to use firewall-offline-cmd while firewalld is operating, it is not advisable because it can only change the permanent configuration that is displayed in firewall after around five seconds.
It’s advisable to use Network Manager, although it is not required. There are several restrictions if Network Manager is not used: firewalld won’t be informed when network devices are renamed. The connections and manually generated interfaces are not restricted to a zone if firewalld is launched after the network has already gone up. They can be added to a firewall-protected zone.-cmd [–permanent] –zone=zone –add-interface=interface, but ensure that the zone set with ZONE=zone in /etc/sysconfig/network-scripts/ifcfg- is the same (or both are empty/missing for default zone); otherwise, the behavior would be unknown.
What are the Directories and Configuration Files on Firewalld?
Firewalld relies on various directories and configuration files to store its rules and settings:
- firewalld.conf: This is the main configuration file located in /etc/firewalld/. It defines global parameters, such as the default zone, runtime configurations, and more. It also includes important settings such as default zone, log options, and the behavior of various firewall components. Adjustments to this file affect the system’s default firewall policies.
- firewalld.zones: A directory that contains XML files for different predefined zones. These zones define the level of trust for network interfaces connected to the system.
How to Configure Firewalld?
- 1. To check its status that the firewalld service is installed, started, and enabled, use the following commands:
- $ sudo systemctl status firewalld
- $ sudo systemctl start firewalld
- $ sudo systemctl enable firewalld
- 2. To check the current configuration, use the following commands:
- $ sudo firewall-cmd –list-all –zone=public
- The commands below allows you to display the open services and ports in the public zone. If desired, you can display the open ports by service or port number:
- $ sudo firewall-cmd –list-services
- $ sudo firewall-cmd –list-ports
- 3. Open a port (in this case port 80 is opened for HTTP) by using the following commands:
- $ sudo firewall-cmd –zone=public –add-service=http
- $ sudo firewall-cmd –zone=public –add-port=80/tcp
- The configuration below is non-persistent and will be gone if the system is rebooted. As noted below, the –permanent flag is needed to save the settings:
- 4. To close a port (in this case port 80 is closed for HTTP), use the following commands:
- $ sudo firewall-cmd –zone=public –remove-service=http
- $ sudo firewall-cmd –zone=public –remove-port=80/tcp
- 5. To reload the configuration, use the following command:
- $ sudo firewall-cmd –reload
- Additionally, if troubleshooting is needed, the following command is entered to display output of debugging firewalld:
- $ sudo firewall-cmd –debug
Common Utilities and Commands in Firewalld:
Firewalld provides a suite of utilities for managing and interacting with the firewall. Some key tools include:
- firewall-offline-cmd: This utility is useful for configuring the firewall when the system is not connected to a network. It modifies the permanent settings without needing to be connected to a live network.
- firewall-config: firewall-config is a graphical utility that allows users to configure firewalld settings easily via a GUI. It is ideal for users who prefer a visual approach over command-line management.
- firewall-applet: The firewall-applet is a tray icon for managing firewalld settings directly from the desktop environment. It is often used for desktop systems and allows users to toggle the firewall status.
- The daemon: firewalld: The firewalld daemon is a service that runs in the background, managing firewall rules based on zones and configurations.
What are Zones and How to Configure Them?
In firewalld, zones represent different levels of trust for network connections. Zones group network interfaces or sources that share the same security characteristics. Some common zones are:
- Predefined Zones: These include zones like public, home, work, dmz, etc., each of which has different default rules.
- Connections, Interfaces, and Sources: Zones are associated with network interfaces, connections, and sources. An interface can belong to a specific zone based on its security level.
- Default Zone: The default zone is applied to all interfaces that are not explicitly assigned to a different zone. This can be set with firewall-cmd –set-default-zone=home.
You can configure zones with commands like:
- $ firewall-cmd –zone=public –add-interface=eth0 (Associates interface eth0 with the public zone).
- Note: Zones define the rules and services that are allowed or blocked. For example, a home zone might allow more traffic (like file sharing or remote desktop) compared to a more restrictive public zone.
What are Services and IPSets in Firewalld?
Service: In firewalld, a service represents a predefined set of rules for a specific application or protocol. Examples include http, https, ssh, and ftp. These can be added to a zone like:
- $ firewall-cmd –zone=public –add-service=http (Opens the HTTP service in the public zone).
- IPSet: An IPSet is a collection of IP addresses or networks that can be used for rules, often for managing large groups of IPs.
- firewall-cmd –permanent –ipset=example_ipset –add-ip=192.168.1.0/24 (Adds an IP range to an IP set).
What are ICMP Type, Helper, and Direct Interface?
- ICMP Type: Specific ICMP types (such as Echo Request or Destination Unreachable) can be allowed or blocked for better control over network diagnostics and responses.
- Helper: Helper modules are used to support connection tracking for protocols like FTP or SIP, which require special handling of dynamic ports.
- Direct Interface: Direct interface allows users to add raw iptables rules directly to the firewalld configuration, offering more fine-grained control over firewall rules.
The Full Summarized List of Commands:
- firewalld: The main service for managing the firewall.
- firewall-cmd: The command-line interface for interacting with firewalld.
- firewall-offline-cmd: Manages permanent configurations offline.
- firewall-config: The graphical configuration tool.
- firewall-applet: A GUI applet for desktop environments.
- firewalld.conf: The primary configuration file.
- firewalld.zone: Configuration for specific zones.
- firewalld.service: Configuration for predefined services.
- firewalld.ipset: Manages IPSets for firewall rules.
- firewalld.direct: Allows direct interaction with iptables.
- firewalld.dbus: Interacts with the D-Bus interface for firewalld.
Conclusion:
Firewalld offers a robust and flexible firewall management system for Linux-based environments. By understanding zones, services, and various commands like firewall-cmd, administrators can configure a highly secure and efficient network environment. Proper use of runtime and permanent configurations, along with the tools and examples provided here, will help you manage firewalls with ease.
References:
- GitHub – firewalld/firewalld: Stateful zone based firewall daemon with D-Bus interface (https://github.com/firewalld/firewalld)
- Documentation | firewalld (https://firewalld.org/documentation/)
- Documentation – Manual Pages – firewall-cmd | firewalld (https://firewalld.org/documentation/man-pages/firewall-cmd.html)
- firewalld – Dynamic Firewall Manager at Linux.org (https://www.linux.org/docs/man5/firewalld.html)
- How to configure firewalld quickly (https://www.redhat.com/en/blog/how-to-configure-firewalld)
- Documentation – Architecture | firewalld (https://firewalld.org/documentation/architecture.html#:~:text=firewalld%20has%20a%20two%20layer,ipset%20and%20the%20module%20loader)