Let’s Encrypt is a nonprofit certificate authority offering free, automated, and open digital certificates for enabling SSL/TLS encryption on websites. It helps secure communications between web browsers and servers by encrypting data exchanged, protecting sensitive information. The service enables HTTPS (SSL/TLS) encryption, increasing web security and reducing administrative burdens. Its short validity period and cost-free nature make it accessible to all websites, regardless of size or budget. HTTPS-enabled sites are seen as more trustworthy by users and major search engines.
What is Let’s Encrypt? A Comprehensive Guide
Let’s Encrypt is a free, automated, and open certificate authority (CA) that aims to make web security accessible to everyone. It offers SSL/TLS certificates that enable secure connections over HTTPS, providing encryption for websites and online services. Let’s Encrypt helps improve privacy, security, and data integrity by issuing trusted certificates that ensure sensitive data remains safe during transmission.
This article will explore how to use Let’s Encrypt, including common questions about its functionality and compatibility with various platforms, including VPS hosting, cPanel, and Home Assistant. We will also address concerns about its security and wildcard certificate support.
Who Uses Let’s Encrypt?
Let’s Encrypt is used by many websites, with around 63.2% of all websites that utilize a known SSL certificate authority relying on it. This includes major websites like Mozilla, Wikipedia, USA Today, and many others. Technically anyone who owns a domain name can use Let’s Encrypt.
How Does Let’s Encrypt Work?
Let’s Encrypt and the ACME protocol enable HTTPS servers to automatically obtain browser-trusted certificates without human intervention. This is achieved by running a certificate management agent on the web server, which proves domain control to the CA and can request, renew, and revoke certificates.
Let’s Encrypt is a security system that identifies server administrators by public key. The agent software generates a new key pair and proves control of one or more domains to the Let’s Encrypt CA. The CA issues challenges to the agent to prove control of the domain, such as providing a DNS record under regularweb.com or an HTTP resource under a well-known URI. The agent must also sign a nonce with their private key pair to prove control of the key pair.
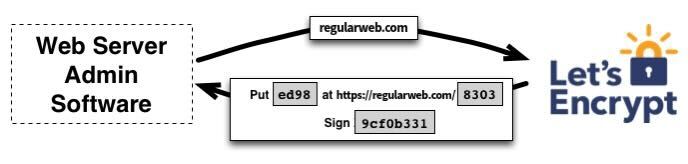
The agent software completes a set of challenges, such as creating a file on a specified path and signing a nonce with its private key. It informs the CA that it’s ready for validation. The CA checks if the challenges have been met from multiple network perspectives, verifies the nonce’s signature, and downloads the file from the web server.
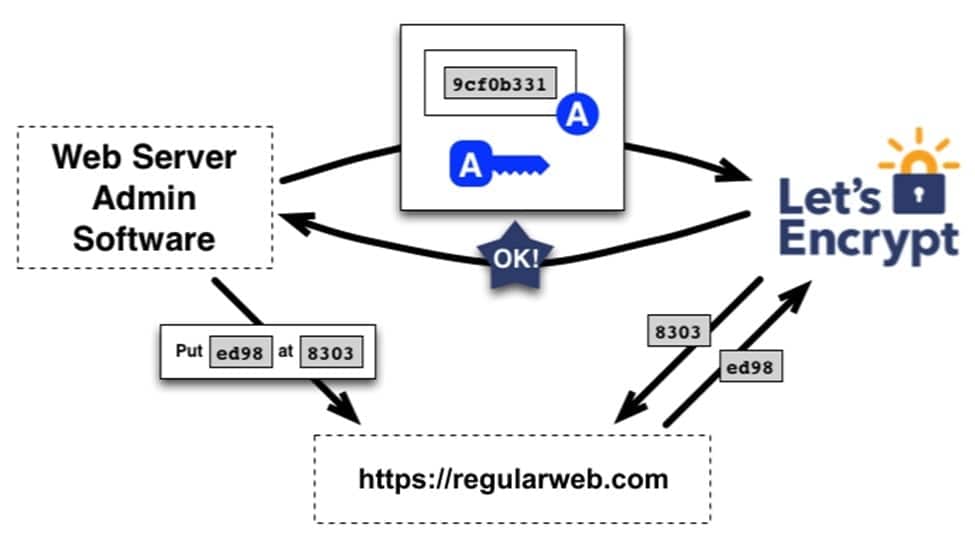
The agent indicated by the public key is permitted to handle certificate management for regularweb.com if the nonce signature is legitimate and the challenges pass. For regularweb.com, we refer to the key pair the agent utilized as an “authorized key pair.”
Certificate Issuance and Revocation
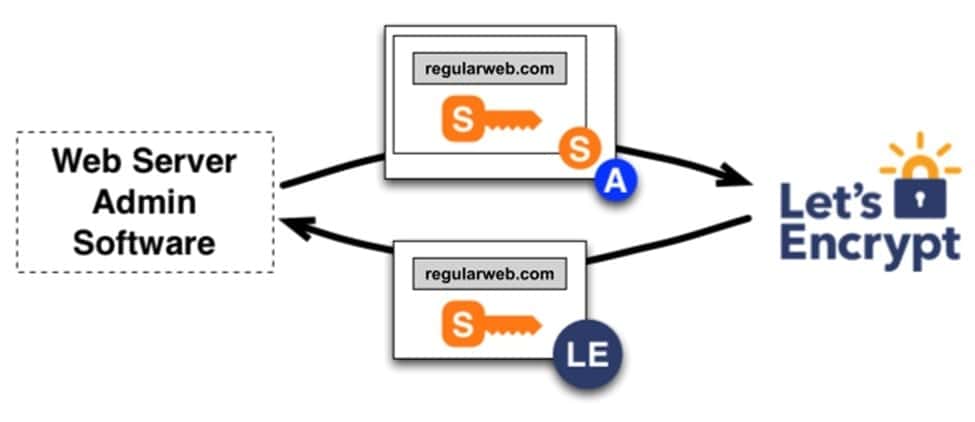
The agent can request, renew, and revoke certificates using an authorized key pair. They created a PKCS#10 Certificate Signing Request, asking Let’s Encrypt CA to issue a certificate for regularweb.com with a specified public key. The agent signs the entire CSR with the authorized key for regularweb.com, ensuring Let’s Encrypt CA is authorized. The CA verifies both signatures and issues the certificate with the public key from the CSR, returning it to the agent. The certificate is then submitted to public Certificate Transparency logs.
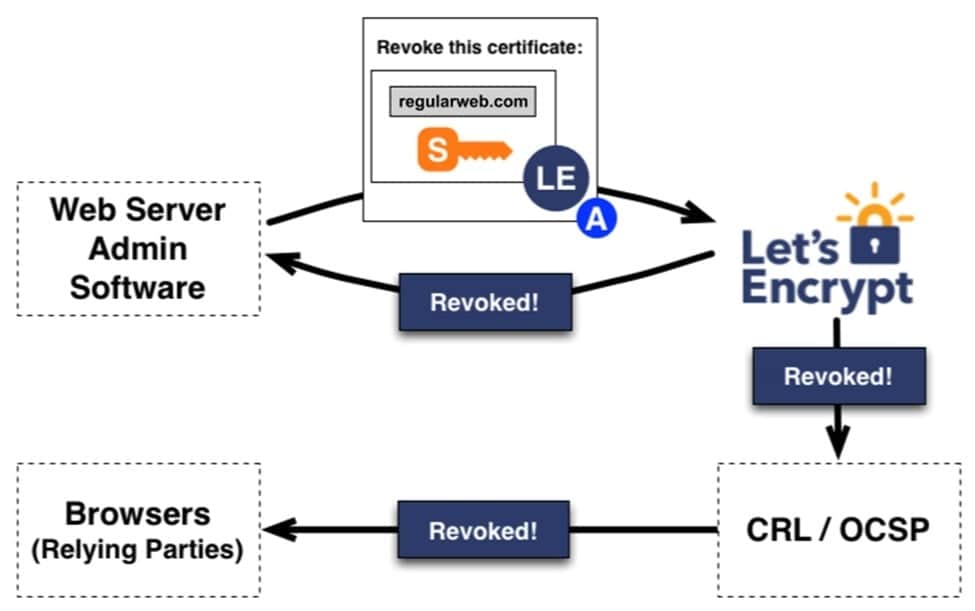
Revocation involves an agent signing a request with an authorized key pair, verifying authorization, and publishing revocation information to OCSP, preventing relying parties from accepting the revoked certificate.
How to Generate a Let’s Encrypt Certificate?
- A. Having a Linux terminal installed: It would be present on a Linux OS. If you are running Windows, install a Linux subsystem (WSL).
- B. Switch to the root user: Root access is required for administrative access. On WSL, switch to the root user to change the default behavior using the following command:
- 1. ubuntu2004.exe config – default-user root (Note: The “ubuntu2004.exe” can be replaced with the version of Linux you are running.)
- C. Install Certbot: Install certbot by running the following commands with the root user:
- 1. sudo add-apt-repository ppa:certbot/certbot
- 2. sudo apt-get update.
- 3. sudo apt-get install certbot
- D. Generate Your Certificate: To generate your certificate, run the command below:
- 1. certbot certonly –manual
- 2. Use the format mywebsite.com when requested to input your domain name, and then click [Y] to accept any additional prompts.
- 3. Lastly, you would need to upload a file to your server to verify ownership in order to receive your certificate. The path to your SSL certificate will then be displayed on the screen when this is finished.
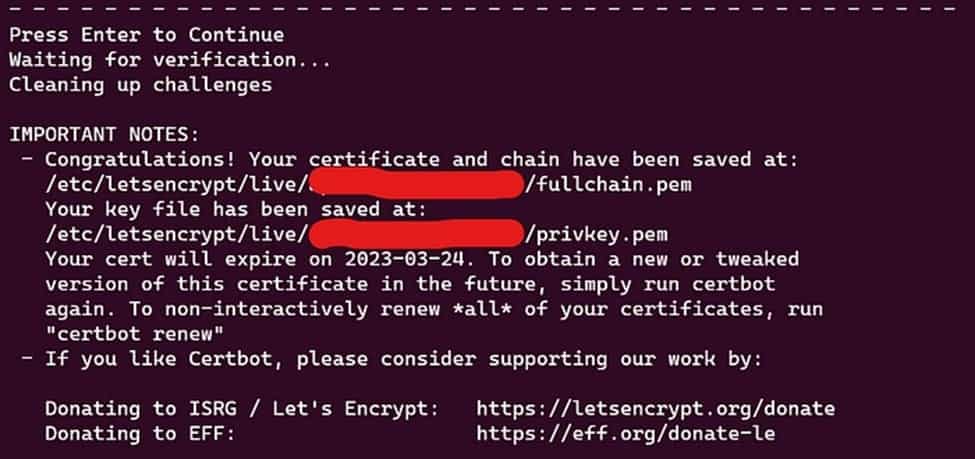
- E. Managing your certificates:
- 1. An access denied message would appear if you were using WSL and attempting to open the certificate file in File Explorer. Use the following command to see the certificate’s contents on your terminal: cat <PATH_TO_CERT>
- 3. You can also use the following helpful commands:
- a. To list all your certificates: certbot certificates
- b. To delete a certificate: certbot delete
- c. To renew your certificate that was generated with “–manual”: certbot certonly –manual -d regularweb.com
- d. If you want to force renewal regardless of the current expiry date: sudo certbot renew –force-renew
- e. To check the expiration date of an Encrypt certificate: openssl x509 -in /etc/letsencrypt/live/your-domain.com/cert.pem -noout -enddate
Does Let’s Encrypt Support Wildcard Certificates?
Yes, Let’s Encrypt does support wildcard certificates. A wildcard certificate allows you to secure multiple subdomains of a domain with a single certificate. For example, a wildcard certificate for * regularweb.com will secure www.regularweb.com and mail.regularweb.com, and other subdomains under regularweb.com. Wildcard certificates are especially useful for businesses or individuals with many subdomains to manage. Previously, wildcard certificates were not supported by Let’s Encrypt, but they are now available with DNS-01 challenge validation.
How to Add a Let’s Encrypt SSL Certificate in a VPS
Adding a Let’s Encrypt SSL certificate to your VPS (Virtual Private Server) can enhance security for your website. The process involves using a tool like Certbot, which automates the issuance and renewal of certificates. Here’s how you can add a Let’s Encrypt SSL certificate to a VPS:
- Install Certbot: You can install Certbot on your VPS using your package manager, such as apt for Ubuntu or yum for CentOS.
- Run Certbot: Execute the Certbot command to obtain a certificate. For example, on Ubuntu, use the following command: sudo certbot –apache
- Configure Your Web Server: Certbot will automatically configure your Apache or Nginx server to use the new certificate.
- Verify the Certificate: Visit your website via https:// to ensure the certificate is installed correctly.
How to Set Up Let’s Encrypt for Home Assistant
Home Assistant, a popular open-source home automation platform, can be secured with an SSL certificate from Let’s Encrypt. Here’s how to set it up:
- Install Let’s Encrypt: Home Assistant can use Certbot or the built-in Let’s Encrypt integration.
- Configure Nginx: Set up a reverse proxy (if needed) with Nginx to handle SSL traffic for Home Assistant.
- Run the Certbot Command: Use Certbot to request a certificate. Use the following command: sudo certbot certonly –standalone -d your-domain.com
- Renew the Certificate: Ensure your SSL certificate renews automatically by adding a cron job to renew the certificate.
Does Let’s Encrypt Auto-Renew?
Yes, let’s enable auto-renewing encryption certificates. The most widely used Let’s Encrypt program, Certbot, automatically initiates a renewal procedure every sixty days (prior to the certificate expiring). If you have properly configured Certbot, your SSL certificate will renew on its own without your intervention.
References:
- How It Works – Let’s Encrypt (https://letsencrypt.org/how-it-works/)
- Renew LetsEncrypt Certificate – Server – Let’s Encrypt Community Support (https://community.letsencrypt.org/t/renew-letsencrypt-certificate/34677)
- Certbot Documentation (https://certbot.eff.org/)
- Home Assistant SSL Setup (https://www.home-assistant.io/docs/ssl/)
- Let’s Encrypt Overview (https://letsencrypt.org/getting-started/)
- cPanel SSL Setup (https://api.docs.cpanel.net/)
- Let’s Encrypt Security (https://letsencrypt.org/certificates/)
- Wildcard Certificate FAQ (https://letsencrypt.org/docs/faq/)